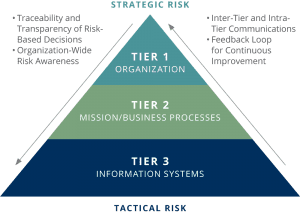
 TAPESTRY is a cloud hosted web application that guides risk assessment for individual organizations of varying complexity. Users can map the business processes together, link their supporting technology, and apply attack scenarios. Utilizing our award-winning approach, TAPESTRY generates quantifiable impacts across three tiers: Information Systems, Mission Business Processes, and the Organization. By connecting your organizational processes to the technology TAPESTRY can identify scenarios that can generate critical risk and help you prioritize resources.
TAPESTRY is a cloud hosted web application that guides risk assessment for individual organizations of varying complexity. Users can map the business processes together, link their supporting technology, and apply attack scenarios. Utilizing our award-winning approach, TAPESTRY generates quantifiable impacts across three tiers: Information Systems, Mission Business Processes, and the Organization. By connecting your organizational processes to the technology TAPESTRY can identify scenarios that can generate critical risk and help you prioritize resources.
Building Blocks
TAPESTRY lays out four essential building blocks that make it possible for organizational leaders to assess a range of interconnected technical, mission, and enterprise risks. It does this by allowing the user to model their organization and link the technology systems to those elements.
- An approach to break apart, organize, and integrate disparate elements of an organization.
- Link business processes together to model how products and services can be.
- Associate organizational functions with information technology (IT) details.
- Lays out a standardized system for identifying attack scenarios and computing the technical, mission, and enterprise risk.
TAPESTRY is a cloud hosted web application that guides risk assessment for individual organizations of varying complexity. Users can map the business processes together, link their supporting technology, and apply attack scenarios. Utilizing our award-winning approach, TAPESTRY generates quantifiable impacts across three tiers: Information Systems, Mission Business Processes, and the Organization. By connecting your organizational processes to the technology TAPESTRY can identify scenarios that can generate critical risk and help you prioritize resources.
Integrated Models
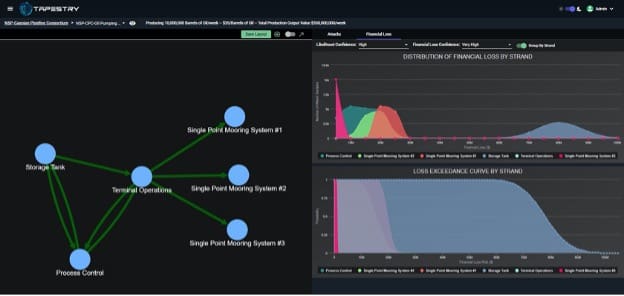
Modern companies are global, integrated, and complex, yet risk assessments tend to focus on specific components and ignore their function in the larger enterprise. Tapestry utilizes graph models to visualize which integrated systems are tied to particular organizational functions. Those systems can be combined, moved, or pulled apart to estimate any number of risk scenarios in your organization. Our consultants use Tapestry to visually represent integrated risk across the range of hacker-induced effects.
Primary and Secondary Effects Estimation
Cyber threats can produce a host of effects from the stealing of corporate data to disruptive attacks against critical infrastructure. Measuring those impacts in a meaningful way requires consistent use of a rigorous method to capture the impact to the targeted system and the resulting financial cost to your organization. Tapestry leverages university-generated research in cyber effects to create standard classifications and estimators which provide a nuanced and meaningful set of metrics for your organization.
Contact Us Today!
Learn more about Tapestry or our Cyber Security Assessment and Consulting Services.
